Trustus AAM
vs Traditional Centralized Access
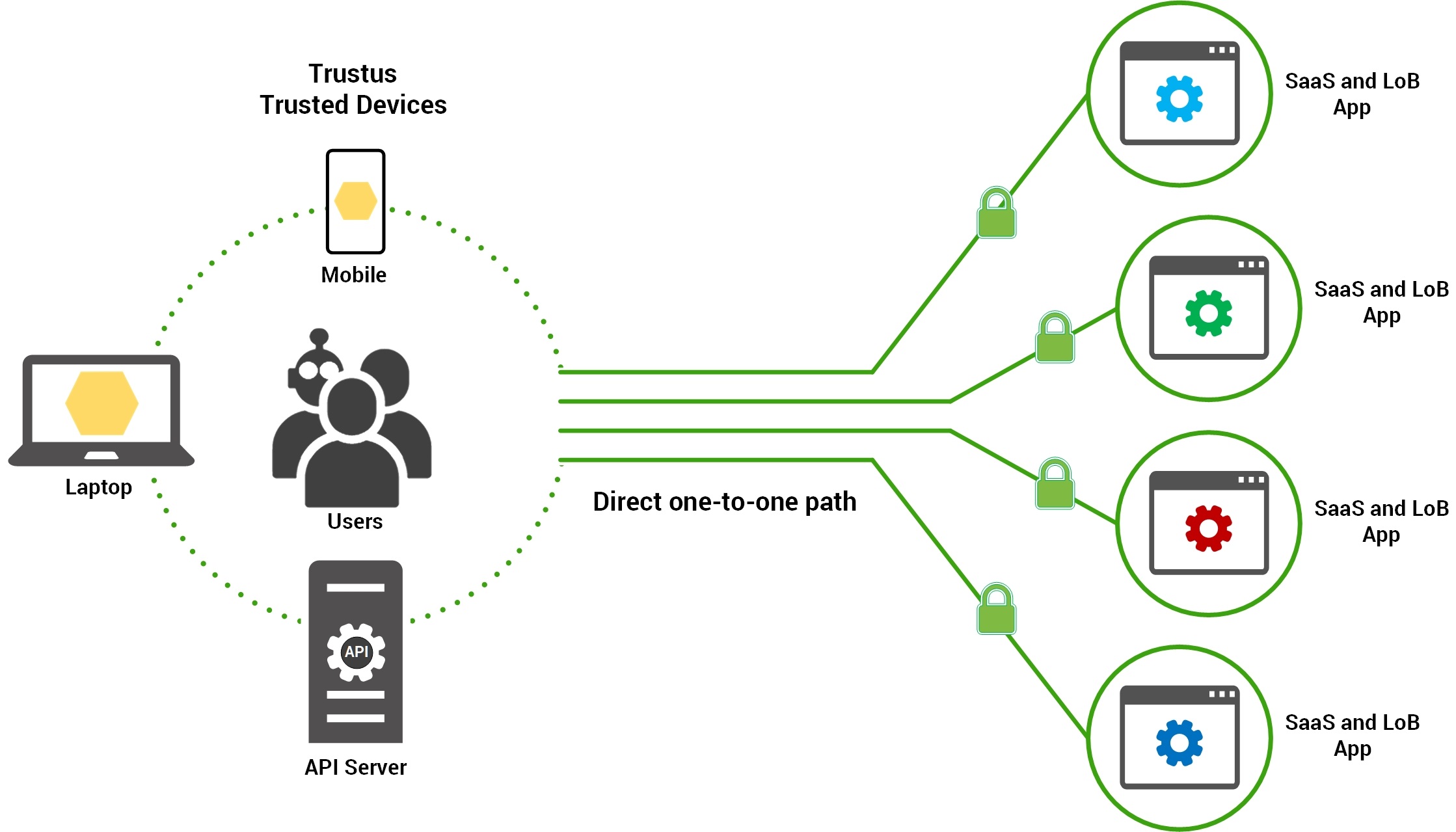
The Decentralized Identity Access Path
Trustus AAM is the foundational
re-architecture that inverts the traditional access model, decisively ending dependency on centralized cloud providers and establishing a separate, resilient identity plane.

The identity model you choose directly determines your enterprise's
security, performance, and ability to stay operational.
How Trustus AAM Ensures Uninterrupted Access
Architectural Independence
Trustus AAM operates in a separate, autonomous domain, and does not rely on Mainframe-on-Internet (MOI) to grant secure access, detaching your identity system from the MOI's central access component.
Direct (Decentralized) Path
We establish a unique, highly-encrypted, direct path from the trusted user's device straight to each SaaS and LoB application, bypassing the MOI's authentication layer.
Maximum Operational Continuity
This independent access architecture delivers maximum operational continuity, ensuring your users maintain seamless access and productivity, even during catastrophic public cloud authentication failures.
Key Benefits:
Resiliency, Security, and Speed
Feature
Business Value
Diferentiator
Decentralized Access Plane
Eliminates the Domino Effect. Users maintain access to applications even during major cloud authentication outages.
Maximum Access Resiliency and business continuity regardless of cloud provider status.
Native Application Fidelity
Pure, Unhindered Functionality. Preserves the application's native features, ensuring users never experience feature loss or compromised performance due to API proxy mediation.
Full Native App Experience with no functional degradation or loss of feature granularity.
Certificate-Based Authentication (CBA)
Structural Defense Identity. The user's certificate is the secure, cryptographically-secured identity, eliminating token theft and phishing vulnerability.
Superior Identity Assurance that exceeds MOI's token-based authentication.
One-Click, Direct Path
Seamless User Experience. Access is established instantly and directly, ensuring an unhindered user workflow without logon prompts or redirects.
Fastest, most resilient access path in the industry.
Trustus AAM
vs Traditional Centralized Access
Trustus AAM
Decentralized Access
Cloud Providers
Centralized Dependency
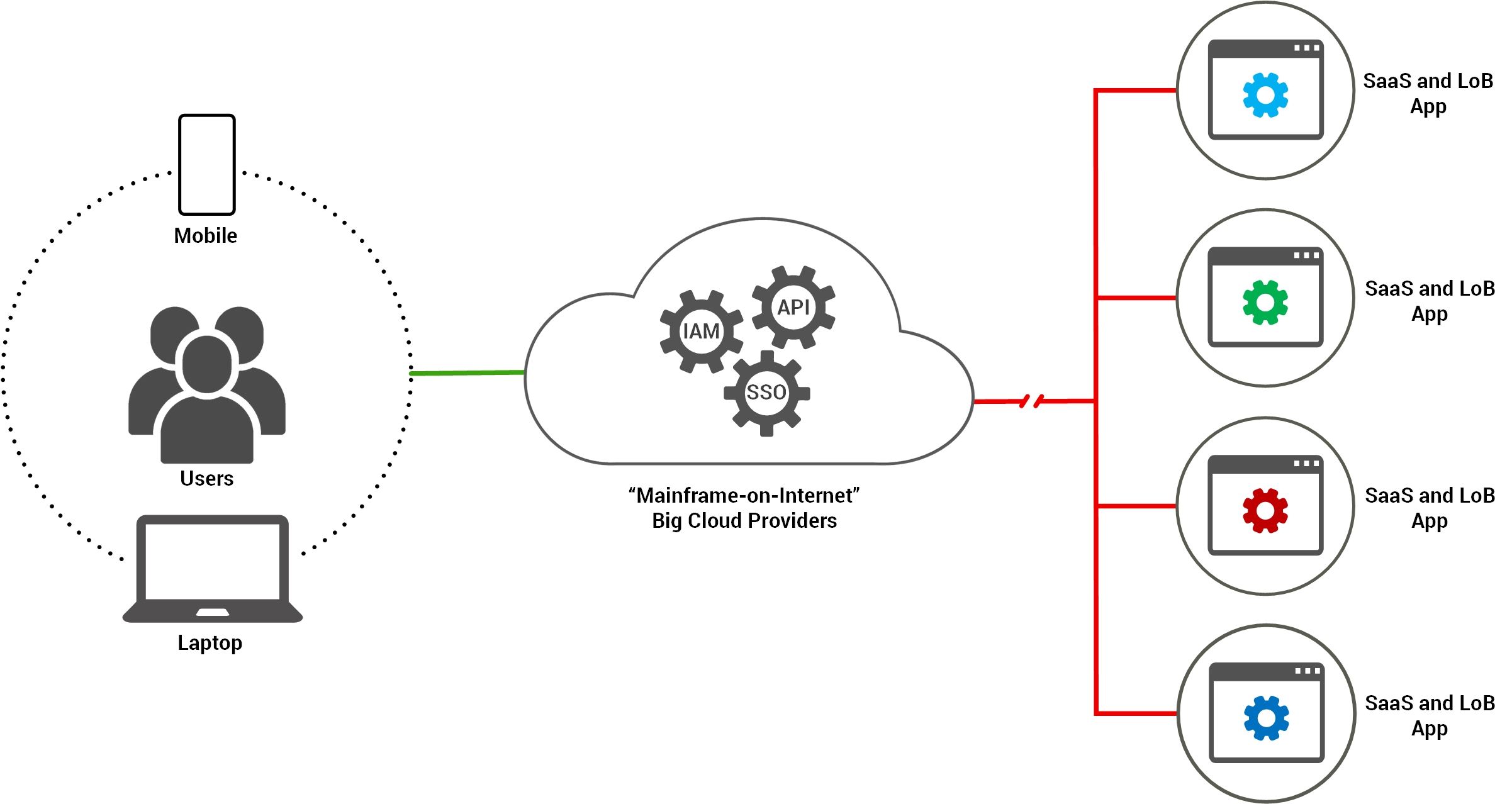
A centralized authentication outage
blocks user access to depenent
applications accross the enterprise.

