Trustus AAM vs Traditional
Certificate-Based Authentication (CBA)
& Certificate-Based Access (CBA)
Zero-Touch Digital Identity
Architecting IT Efficiency
A Service Redefined
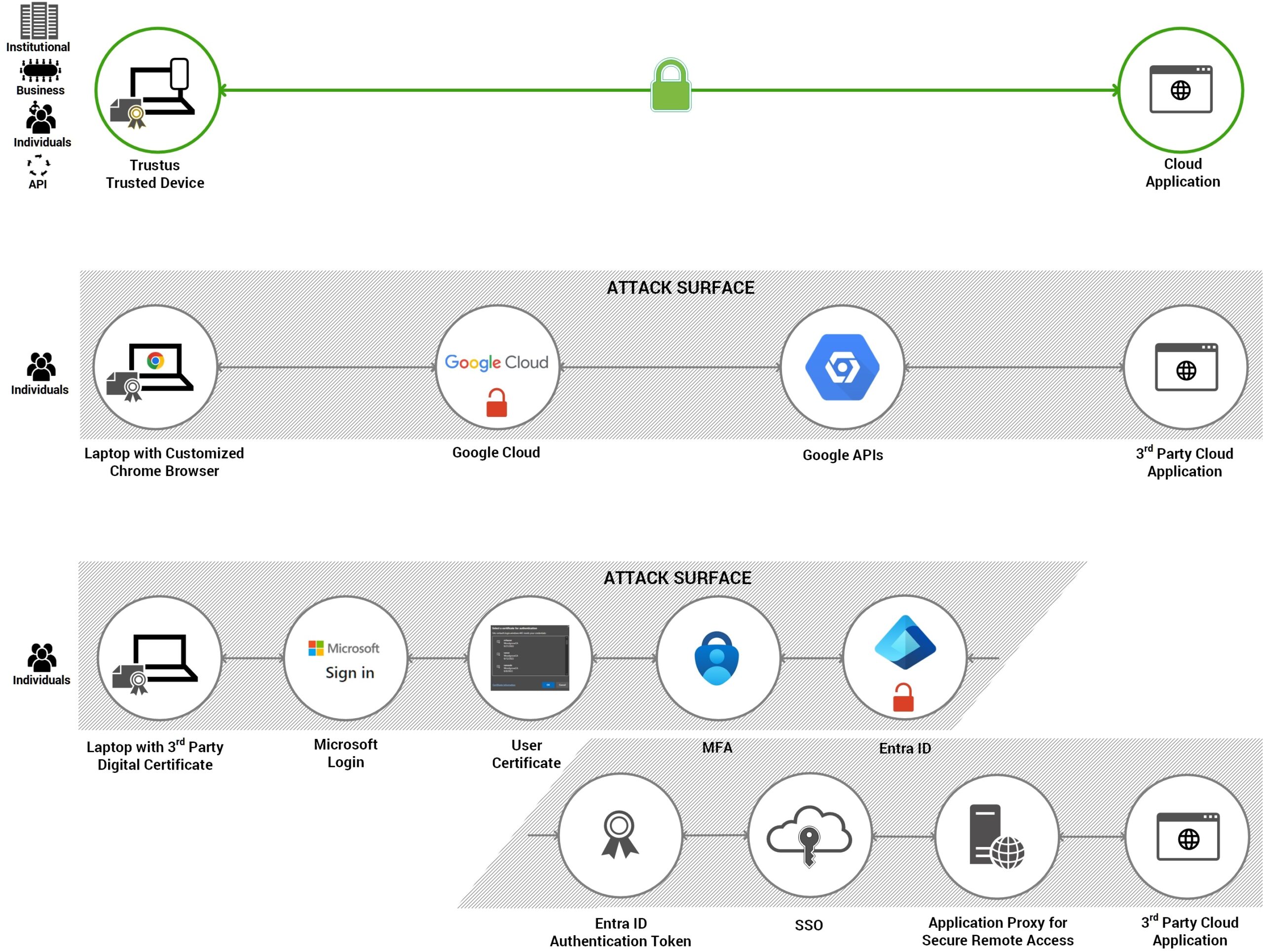
Trustus AAM delivers superior Digital Identity (Machine Identity) management by design, immediately replacing the administrative drag of traditional CBA models offered by centralized cloud providers with automated simplicity and strategic control.
The Trustus AAM Advantage
Automated Digital Identity Service
A superior DI service built for operational agility,
control, and user satisfaction.
One Click.
Digital Identity Driven Access
You’re In.
Digital Identity Lifecycle
Trustus AAM's Automated Service
Strategic Outcome
Onboarding & Deploymentty
Certificate provisioning and device onboarding are seamless and fully automated, requiring no manual IT intervention (a stark contrast to the complexity of legacy MOI CBA models).
Accelerated Time-to-Value and significant reduction in administrative costs.
Maintenance & Revocation
Lifecycle management is proactive, automated, and continuous, supporting instant, granular controls, including the industry-first option for temporary service revocation for emergency or routine needs.
Zero-Touch Maintenance and elimination of administrative error and certificate-expiration risks.
User Experience
The secure identity process is invisible to the user, providing a truly frictionless, one-click experience for access.
Maximum User Productivity and full user adoption of secure access controls.
Scalability
The fully automated service is built for high-volume environments, enabling unconstrained scaling across the globe.
Future-Proof Growth without resource constraints or increased operational expense.
Communicating with your Apps
You're Safe.
Trustus AAM
One-to-One Path – Decentralized Access
Traditional CBA
Token Exchange – Centralized Access
Source-Initiated Identity Verification
The user's endpoint certificate acts as the direct catalyst for identification.
Source authentication
The process uses the user's certificate for the initial identity check.
Continuous, Direct Connection
The validated certificate is used to identify the source and maintain a continuous, direct connection to the target application via the Trustus Privacy Bridge.
The Transition
The authenticated certificate is immediately exchanged for a session token to manage the user's access session.
Unphishable Identity
Your access is governed by the persistent,
unphishable machine identity, not by a breakable token.
The Consequences
This architectural shift breaks the continuous link to the persistent machine identity.
Strategic Outcome
This process secures Sovereign Access for your enterprise.
The Risk
It reintroduces dependency on a centralized authentication and access system, creating a potential Single Point of Failure (SPOF).
Trustus AAM
vs Traditional CBA
Trustus AAM
Google CBA
Microsoft CBA