Trustus AAM is
The Superior Passwordless Solution
Structural Defense:
Ending the Password-Based Era
Trustus AAM delivers the definitive, superior
passwordless solution by establishing a
foundational Structural Defense that
eliminates the entire class of
compromise in traditional
authentication methods.
The Limitations of Passwords and Biometrics
Vulnerability
Passwords and derived tokens are phishable and,
once stolen, can be used by an attacker anywhere.
False Security
Biometrics are static, un-resettable passwords. They are non-secret credentials that are permanently compromised if stolen.
Non-Cryptographic Identity
Biometrics lack the security of a digital identity; they are not cryptographic machine identities and cannot use a certificate-based key to validate the user's endpoint.
The MFA Trap
Even within traditional Multi-Factor Authentication (MFA), the security chain remains vulnerable because it is only as strong as its weakest, most phishable factor.
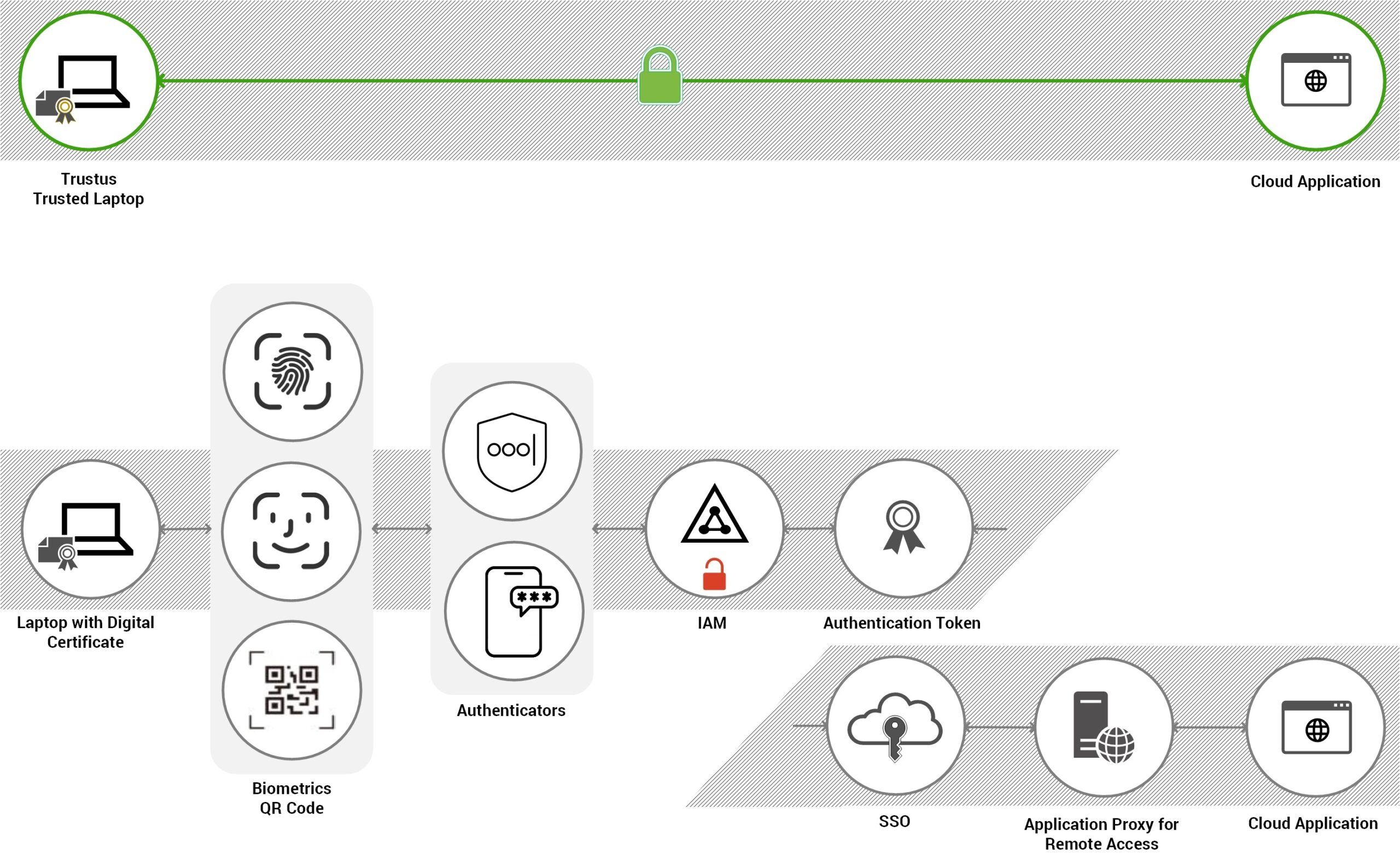
Trustus Cryptographic Identity
vs Password Authentication
Review this comparison to understand why Trustus
Cryptographic Identity is the uncompromisable,
next-generation approach:
Security Dimension
Traditional Password Authentication (Incl. Biometrics & Tokens)
Trustus AAM Cryptographic Machine Identity (CBA)
Identity Core
Relies on shared secrets (passwords) or static identifiers (biometrics) that can be stolen or copied.
Relies on a unique, private X.509 Certificate Key (Digital Identity) that cannot be shared or stolen.
Phishing / Spoofing
High Risk: Credentials are phishable; biometrics are spoofable; tokens are interceptable.
Zero Risk: The machine identity is unphishable and the cryptographic key cannot be spoofed.
Resettability
Passwords can be reset, but biometrics are permanent and un-resettable if compromised.
The identity key is managed within an automated, continuous lifecycle, allowing for secure, zero-touch replacement.
MFA Effectiveness
Limited by the weakest, most phishable factor (the password), leaving the system vulnerable to MFA bypass attacks.
Not Subject to MFA Flaws: Authentication is the first and only factor, providing Structural Defense by replacing the flawed approach entirely.
Trustus AAM
vs Traditional Passwordless Access
Trustus Passwordless Access
Traditional Passwordless
Access