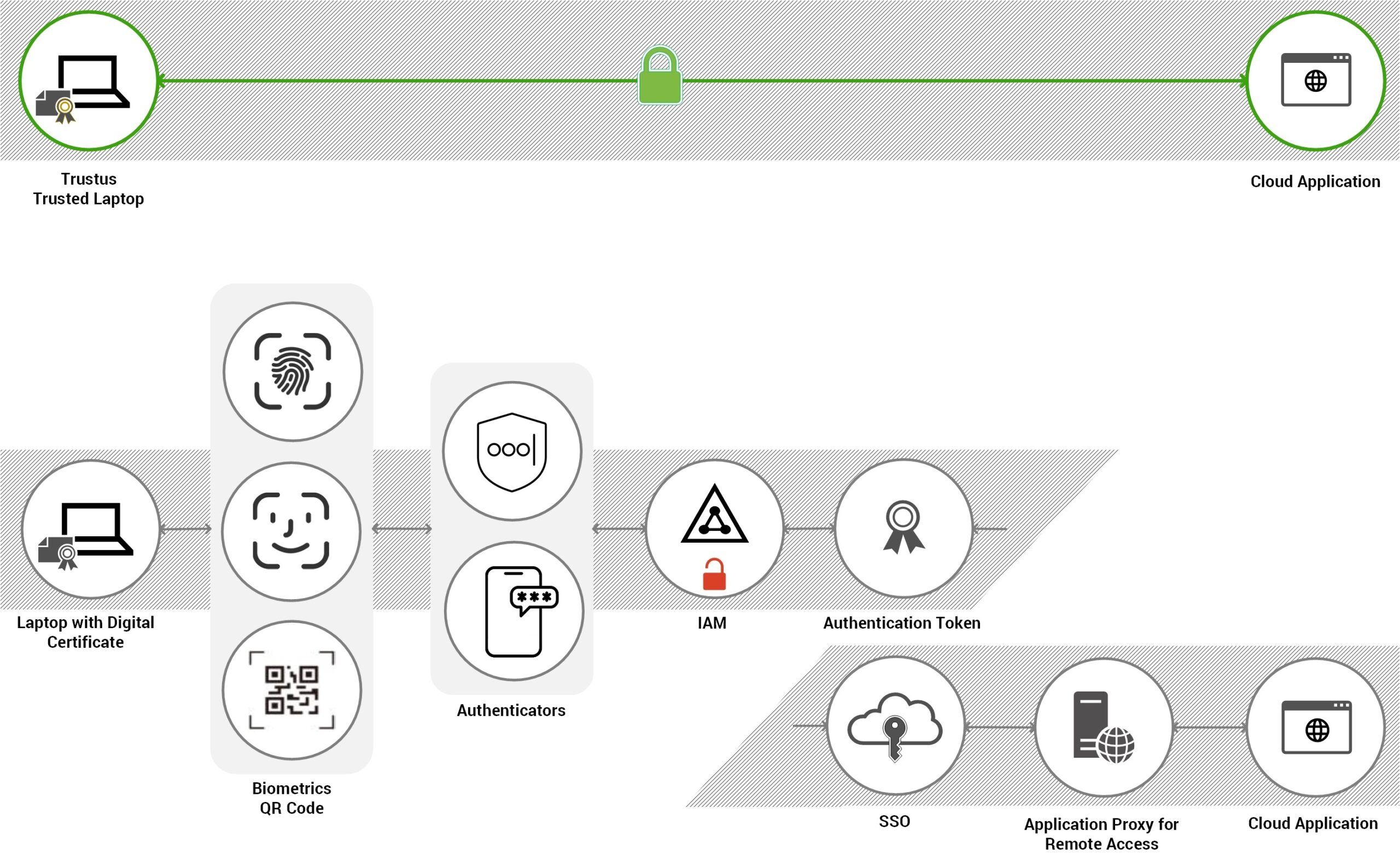
Passwordless
Access:
Zero Touch
Encrypted
Direct
No 2FA, no biometrics,
and no authenticator apps.
Eliminate passwords, proxies,
and manual certificates.
Experience instant, secure, direct-to-application
access with Trustus proprietary automation.
Trustus Zero Touch
Onboarding Millions with Absolute Assurance
Eliminate Manual Risk.
Achieve Instant Identity Trust.
Zero Touch means the entire identity process from initial validation to cryptographic deployment
is handled instantaneously and securely by the system, eliminating manual steps that introduce
human error, cost, and risk.
Trustus ensures every identity is instantly and correctly onboarded with Foundational Trust:
Feature
How Trustus Automates
Benefit to Your Business
Instant Identity Validation
The Trustus system automatically performs real-time validation of the user's identity and confirms the device/endpoint meets the customer's contractual security posture (e.g., proper IP range, required AV/patch compliance) before a certificate is issued.
Eliminates Human Error and Risk. Ensures cryptographic trust is only granted to entities operating under the customer's defined, pre-validated security posture.
Instant Identity Validation
The Trustus system automatically performs real-time validation of the user's identity and confirms the device/endpoint meets the customer's contractual security posture (e.g., proper IP range, required AV/patch compliance) before a certificate is issued.
Eliminates Human Error and Risk. Ensures cryptographic trust is only granted to entities operating under the customer's defined, pre-validated security posture.
Secure, Native Provisioning
Ultra-secure X.509 certificates are securely and automatically issued and deployed directly from the exclusive, native Trustus CA to the required endpoint.
Bypasses Friction and Delay. Drastically reduces friction and time-to-trust by eliminating manual Certificate Signing Request (CSR) handling and installation steps.
Universal Endpoint Scope
This Zero Touch process applies comprehensively to all heterogeneous endpoints across your environment.
Enables True Foundational Trust. Every identity - from users, laptops, and wearables to IoT devices and API/EDI processes - is secured under the same, high-assurance X.509 standard.
Policy-Driven Enforcement
The entire operation is strictly governed by pre-defined corporate policies that are enforced at the point of issuance, ensuring immediate compliance.
Compliance is Baked In. Every new certificate instantly meets internal standards, FIPS 140-2 requirements, and regulatory mandates (like SOX/eGRC), without requiring retrospective audits.
Trustus AAM
vs Traditional Passwordless Access
Trustus Passwordless Access
Traditional Passwordless
Access