Secure Access Platform
Application Access Management (AAM)
Trustus unifies your security posture by building Foundational Trust
into every identity, eliminating the most persistent threats accross
your modern, distributed enterprise.
Experience the Power of Trustus AAM
Defines next generation ZTA Advanced Intelligence Security model
Enterprise Risk ERM
Secure Service Edge (SSE)
holistic protection for an overall risk and resilience comprehensive approach.
Cyber Resilience
Proactive and Adaptive
safeguards for business services and data against dynamic threats, ensuring uninterrupted access, and secure connectivity for all users and devices.
Data Protection
Verify Sender/Receiver
identity, secure application access, and implement two-way encryption to prevent data modification and exfiltration.
Zero Trust Cloud
Identity-Centric SSE Focus
on user and device identity as the primary security perimeter, enables granular certificate-based access control and continuous authorization and authentication.
Strategic ERM to Tactical ZTA
Trustus AAM
Data Loss Prevention DLP
Security Service Edge (SSE)
Architecture unifying identity, authentication
and access in a single cohesive stream.

Key Features of Trustus AAM
Work smarter, not harder
Trust humans and machines to access work and leisure applications directly from anywhere with X.509 Root-Signing Certificate Authority
and Zero Trust Architecture. Eliminates real threats, like malware and credential theft.
Full visibility
Every Trustus certificate is easily visible using real-time CA CRL (certificate revocation list) synchronization. No network scanning
or discovery of key and trust stores.
Mission drivers and search
Tag and group certificates logically using mission driven certificate attributes. Instantly find the certificate, digital signature and status
you need.
Granular controls
Certificates set permissions that the Privacy Bridge controls. Users
and groups can access or be denied application access temporarily, periodically, with reinstatement of rights, or permanent termination.
Certificate delivery at scale
Automatically deploy user-side certificates to one or many hetero-
geneous user groups in real-time without agent or client.
Real-time connection control
Real-time command and control of shutdown or reinstatement of connection to services for user groups or individuals.
Agentless and clientless
Agentless and clientless solution eliminates attack surfaces and identity validation failures, while leveraging lean, identity-driven mTLS for robust threat prevention.
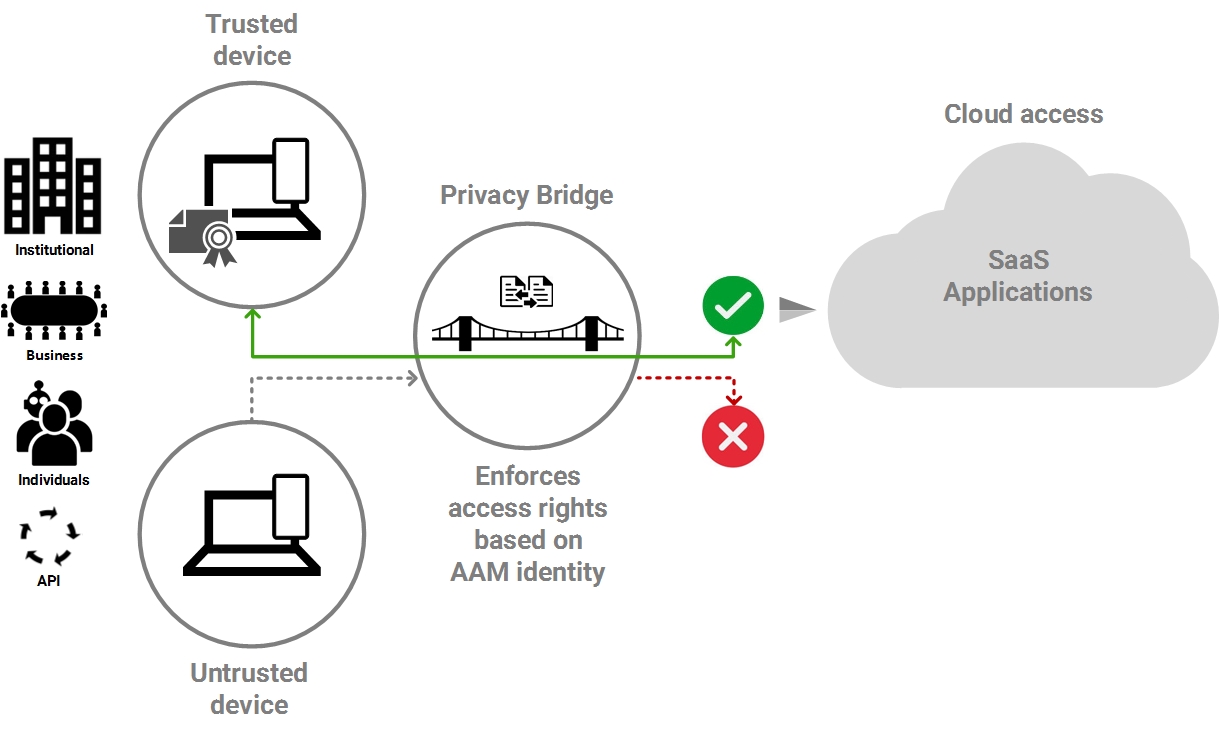
Privacy Bridge
Controlled pass-through for approved users with valid X.509 certificates. Full privacy. Intruders are blocked. No data inspection. Seamless access, frictionless connectivity.
Privatized tenant URL access
Humans, devices, machines, IoT, AI routines, and transactional data flows gain approved access to critical applications via ‘privatized’ tenant URL connections.
Two-way encryption
mTLS achieves two-way encryption with FIPS 140-2 certified crypto-library.
Reporting and alerts
Generate custom or out-of-the-box reports, send alerts via email or chat tools, and renew, suspend, reinstate, revoke, or drill down into certificate details with a simple right-click.
Provenance
Unambiguous proof events occurred and who did them. SOX audit, pharma, research, and data aggregation are examples of digital lineage.
Trustus AAM
Your journey.
Make it safe.
Cloud
Single or
Multi-Tenant
Privatized Tenant
Access
Hybrid
Public or Private
Cloud
Private Browser
Access
On-prem
Hosting
To the Edge
Enterprise licenses with SME price ramp
Powered by
Trustus
Trustus is where you exist online

