Trustus AAM
Fortifying Your Existing SSL VPN Investment
Trustus AAM wraps your existing SSL VPN Concentrator with
proactive Universal Zero Trust security control.
Instantly eliminates the VPN's greatest risk source,
the compromised credential, while preserving your
entire investment.

SSL VPN is overshadowed by its greatest risk:
phishable credentials. Trustus AAM is the solution.
How Trustus AAM Protects the SSL VPN
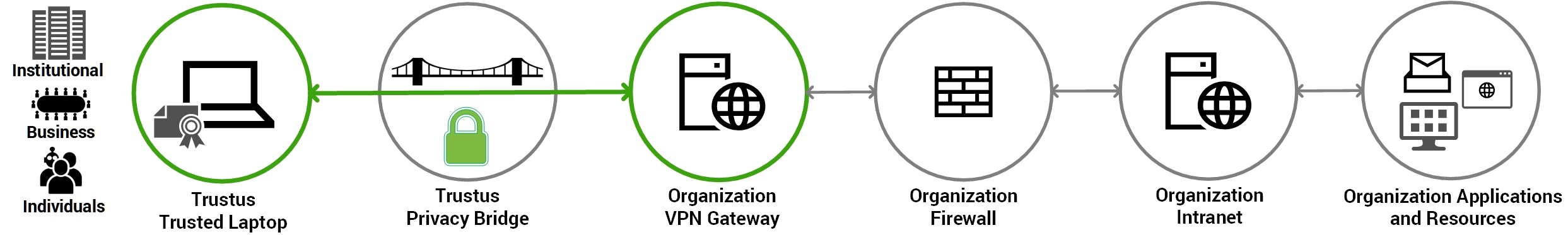
Trustus AAM solves the identity problem by seamlessly inserting an
Unphishable Cryptographic Identity (CBA) check into the VPN access flow.
Replaces Phishable Credentials
Trustus AAM wraps the login request before it hits the VPN concentrator.
It bypasses the VPN's weak password/ token prompt and checks for a Cryptographic Machine Identity (X.509 certificate) installed on the trusted device.
Verifies Identity and Posture
The platform validates the key's authenticity, ensuring access comes from a verified, unphishable machine identity.
Grants Uncompromised Access
Upon successful cryptographic verification, Trustus AAM connects the user securely to the VPN Concentrator, allowing safe user access granted with the strongest form of identity assurance.
Benefits for the VPN User and the Organization
Trustus AAM immediately turns your SSL VPN from a vulnerability into a structurally
protected resource.
Stakeholder
Benefit
Trustus AAM’s Action
The Organization (Risk)
Structural Risk Elimination.
Structurally eliminates the vulnerability to phishing and credential theft that targets the VPN login; the root cause of most remote access breaches.
The Organization (Financial/IT)
ROI on Sunk Costs & Stronger ITGCs.
Preserves the investment in existing VPN hardware and integration, delaying rip-and-replace cycles while strengthening SOX 404 compliance controls.
VPN User
Frictionless, Passwordless Experience.
The user no longer needs to enter phishable passwords or manage MFA tokens. Access is silent, secure, and automatic once the device is trusted.
Technical Implementation: Zero-Disruption Fortification
Trustus AAM is designed for non-disruptive integration.
Leveraging standards and protocols to seamlessly insert the
cryptographic control layer between the user and the SSL VPN.
Existing Infrastructure
Requires no changes to your existing VPN Concentrator hardware (Cisco, Palo Alto, etc.). Trustus AAM simply acts as the Identity Provider (IdP) for the VPN's authentication process.
Cryptographic Identity
Trustus AAM manages and issues the necessary X.509 Certificates directly to authorized user machines, completely eliminating the need for complex, manual PKI management.
Agentless Architecture
Requires no agents or persistent software installations on the user's endpoint to enable the cryptographic check.

Trustus AAM for SSL VPN
Trustus AAM for SSL VPN
vs Traditional IPsec VPN
Feature
Trustus AAM for SSL VPN
Traditional IPsec VPN
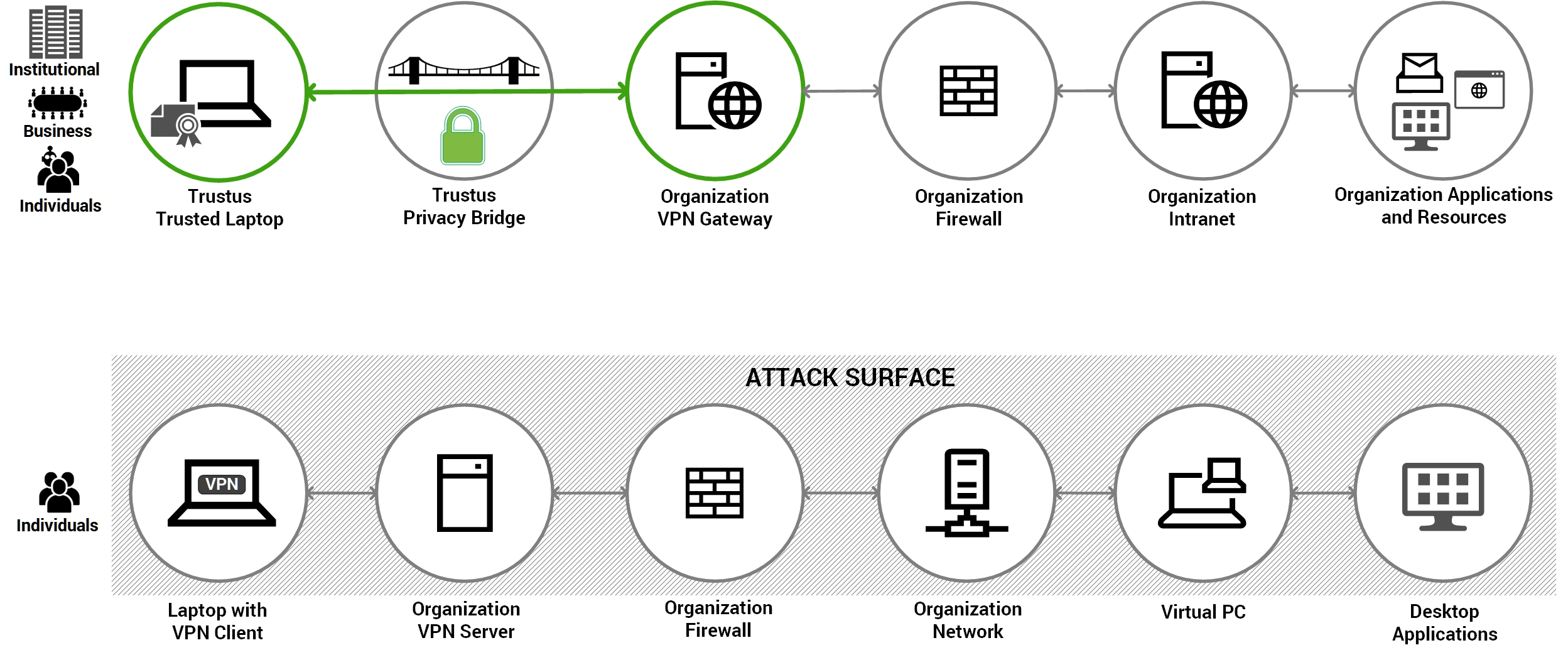
Access Model
Trustus Privacy Bridge Controlled Access. Provides direct web browser access to corporate internet VPN gateway to authorized and active users only. Unauthorized and inactive users and web crawler bots never gain access to the corporate VPN gateway.
Corporate Network Access. Grants broad access to
the entire internal network once connected, regardless of the specific application needed.
Trust Model
Zero Trust (Never Trust, Always Verify). Continuously verifies every user and device for every access attempt, regardless of location, eliminating implicit trust.
Implicit Trust. Assumes trust once a user is authenticated and connected to the network, allowing free movement within the perimeter, leading to unauthorized access.
Client/Deployment
Agentless & Clientless. Operates seamlessly without requiring any software installation on user devices, simplifying deployment and management.
Client-Based. Typically requires installing and managing a dedicated VPN client software on each user device.
Attack Surface
User-Unique. Abolishes the attack surface by creating secure, user personalized tunnel, hiding the network from unauthorized view.
Broad Network Exposure. Increases the attack surface by extending the internal network perimeter to remote users, making it vulnerable to lateral movement if compromised.
Authentication
and Security
User Certificate-Driven & Two-Way Encrypted mTLS. Employs 100% phish-resistant, cryptographically strong X.509 certificates for authentication, establishing a private, unbreakable, two-way encrypted tunnel.
Relies on passwords or shared secrets and pre-installed tokens, which can be phishable or compromised.
Trustus AAM for SSL VPN
vs Traditional IPsec VPN
Trustus AAM
for SSL VPN
Traditional
IPsec VPN