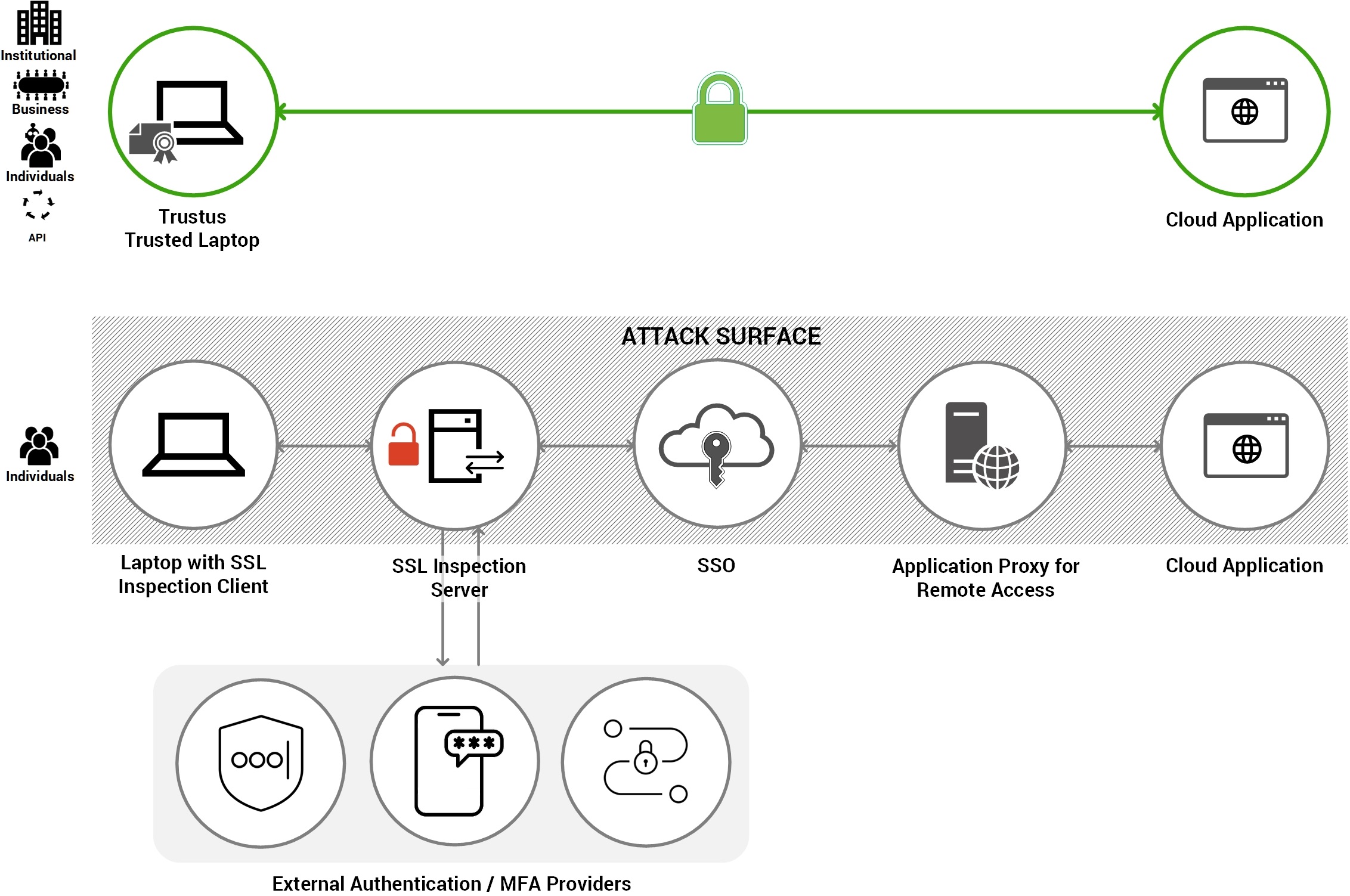
Trustus AAM is the End of
Inspection
Structural Defense ensures
Absolute Data Confidentiality.
Cryptographic Identity ensures connection
integrity.

Review the structural comparison:
Feature
Trustus AAM's Approach
Traditional SSL/TLS Inspection
Philosophy
Zero Trust: Authenticate the identity of the sender at the source; never inspect data content centrally.
Trust-but-Verify: Decrypt all traffic at a central proxy to verify its content before re-encrypting.
Authentication Core
Relies on cryptographic Machine Identity (CBA/X.509); the identity is the core authentication.
Relies on tokens/passwords to initiate sessions; decryption/inspection is applied centrally afterwards.
Decryption Point
None: Data remains encrypted end-to-end; traffic is forwarded in its original state.
Central Choke Point: Data is decrypted and held in plaintext on a firewall or proxy.
Data Privacy
Absolute Confidentiality: Data flow content is never inspected or stored in plaintext by Trustus AAM.
Privacy Violation Risk: Decrypted content is exposed in plaintext to internal compromise and regulatory risk.
Security Risk
Low: Data remains encrypted, eliminating the centralized decryption risk entirely.
High: The central decryption device creates a Single Point of Compromise (SPOC).
Experience
Frictionless and Seamless for users and admins; no latency or application breakage.
High latency, complexity, and application failures due to certificate manipulation.
Trustus AAM
vs SSL Inspection
Trustus AAM
Data Confidentiality
Direct Access
SSL Inspection
Data Interception
Indirect Access