Trustus AAM
vs Traditional VPN
Unphishable Access and Risk Containment
The traditional VPN creates a massive risk gap: it forces you to use weak keys for
authentication and grants attackers broad network access if breached. Trustus AAM
eliminates both of these critical flaws.
We replace fragile authentication with unphishable machine identity and ensure access
is contained to a single application (e.g. virtual desktop), collapsing your attack surface
and delivering verifiable TCO reduction.
Foundational Access:
Feature
Trustus AAM
Traditional VPN
Access Model
Application-Level Access. Provides granular access only to the specific applications and resources a user
is authorized for, never granting broad network access.
Corporate Network Access. Grants broad access to the entire internal network once connected, regardless of the specific application needed.
Trust Model
Zero Trust (Never Trust, Always Verify). Continuously verifies every user and device for every access attempt, regardless of location, eliminating implicit trust.
Implicit Trust. Assumes trust once a user is authenticated and connected to the network, allowing free movement within the perimeter.
Client/Deployment
Agentless & Clientless. Operates seamlessly without requiring any software installation on user devices.
Client-Based. Typically requires installing and managing a dedicated VPN client software on each user device.
Attack Surface
User-Unique. Abolishes the attack surface by creating a secure, user-personalized tunnel, hiding the network from unauthorized view.
Broad Network Exposure. Increases the attack surface by extending the internal network perimeter to remote users.
Authentication
and Security
User Certificate-Driven & Two-Way Encrypted mTLS. Employs 100% phish-resistant, cryptographically strong X.509 certificates.
Relies on passwords or shared secrets, which can be phishable or compromised.
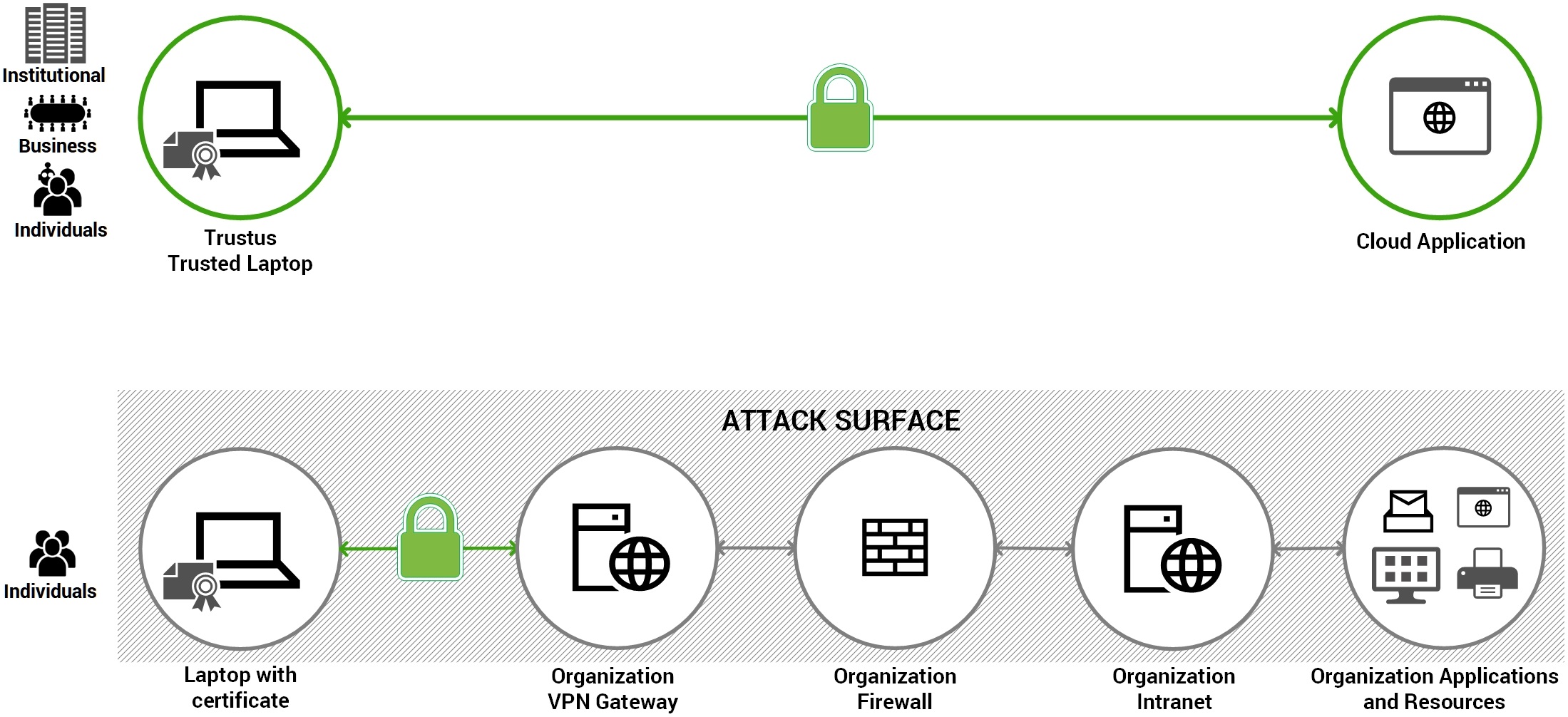
The Structural Advantage:
Application Access, Not Network Tunnels
The IPsec VPN is designed for creating a network tunnel; Trustus
AAM is designed for secure, private application access.
We never grant the user a network address or route users through your core network.
We identity cryptographically and connect them directly to the application.
This is the difference between giving a user an IP address inside your perimeter and
granting a single, protected key to a single vault.
Trustus AAM Converting Network Risk into
Application Access
Legacy Stack Challenge
Legacy IPsec VPN Risk
Trustus AAM’s Structural Defense
Executive Outcome
Identity Risk
Relies on phishable credentials or fragile Pre-Shared Keys (PSKs). Identity theft grants network entry.
Replaced by Unphishable Cryptographic Identity. Access tied to an irreversible key managed seamlessly by Trustus.
Eliminates Credential Risk: Access cannot be phished, removing the primary attack vector.
Access Risk
Grants broad Network Access. User is routed inside the network, enabling dangerous lateral movement.
Enforces Zero-Trust Application Access. Access is granted only to the specific resource needed, bypassing network routing.
Eliminates Lateral Movement:
Network segmentation is inherent, containing any compromised device.
Infrastructure Cost
Requires costly, centralized VPN Concentrator Hardware/ Software licenses to terminate tunnels.
Agentless and Decentralized. Access is managed at the application edge, retiring the need for central gateway hardware.
Significant TCO Reduction:
Eliminates CapEx and OpEx associated with network concentrators.
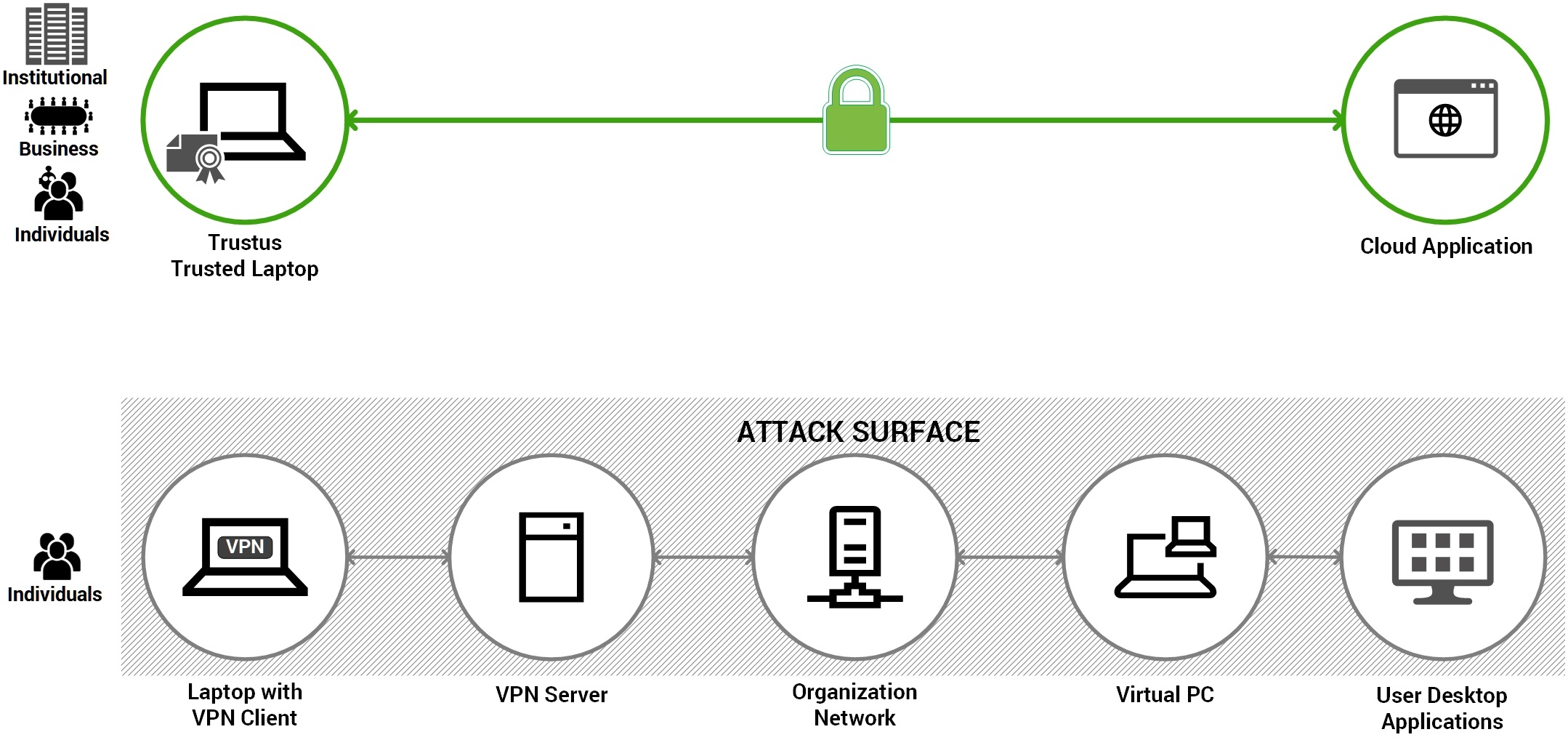
Trustus AAM
vs Traditional IPsec VPN
Trustus AAM
Traditional
IPsec VPN
SSL VPN is overshadowed by its greatest risk:
Phishable Credentials.
Trustus AAM is the answer.
Trustus AAM
vs Traditional SSL VPN
Trustus AAM
Traditional
SSL VPN