Trustus AAM
Fortifying Your Existing SSL VPN Investment
Trustus AAM wraps your existing SSL VPN Concentrator with
proactive Universal Zero Trust security control.
Instantly eliminates the VPN's greatest risk source,
the compromised credential, while preserving your
entire investment.

SSL VPN is overshadowed by its greatest risk:
phishable credentials. Trustus AAM is the solution.
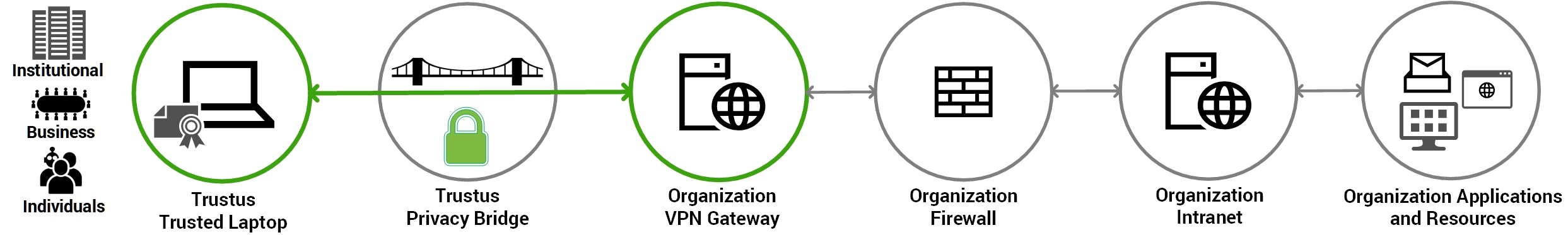
How Trustus AAM Protects the SSL VPN
Trustus AAM solves the identity problem by seamlessly inserting an
Unphishable Cryptographic Identity (CBA) check into the VPN access flow.
Replaces Phishable Credentials
Trustus AAM wraps the login request before it hits the VPN concentrator.
It bypasses the VPN's weak password/ token prompt and checks for a Cryptographic Machine Identity (X.509 certificate) installed on the trusted device.
Verifies Identity and Posture
The platform validates the key's authenticity, ensuring access comes from a verified, unphishable machine identity.
Grants Uncompromised Access
Upon successful cryptographic verification, Trustus AAM connects the user securely to the VPN Concentrator, allowing safe user access granted with the strongest form of identity assurance.
Benefits for the VPN User and the Organization
Trustus AAM immediately turns your SSL VPN from a vulnerability into a structurally
protected resource.
Stakeholder
Benefit
Trustus AAM’s Action
The Organization (Risk)
Structural Risk Elimination.
Structurally eliminates the vulnerability to phishing and credential theft that targets the VPN login; the root cause of most remote access breaches.
The Organization (Financial/IT)
ROI on Sunk Costs & Stronger ITGCs.
Preserves the investment in existing VPN hardware and integration, delaying rip-and-replace cycles while strengthening SOX 404 compliance controls.
VPN User
Frictionless, Passwordless Experience.
The user no longer needs to enter phishable passwords or manage MFA tokens. Access is silent, secure, and automatic once the device is trusted.
Technical Implementation: Zero-Disruption Fortification
Trustus AAM is designed for non-disruptive integration.
Leveraging standards and protocols to seamlessly insert the
cryptographic control layer between the user and the SSL VPN.
Existing Infrastructure
Requires no changes to your existing VPN Concentrator hardware (Cisco, Palo Alto, etc.). Trustus AAM simply acts as the Identity Provider (IdP) for the VPN's authentication process.
Cryptographic Identity
Trustus AAM manages and issues the necessary X.509 Certificates directly to authorized user machines, completely eliminating the need for complex, manual PKI management.
Agentless Architecture
Requires no agents or persistent software installations on the user's endpoint to enable the cryptographic check.

Trustus AAM for SSL VPN